A new law went into effect for 2020 in California that is having global IT ecosystem ramifications. Specifically, California mandated devices that can be connected to a network to have reasonable security features to protect the device by default. In other words, the days of classic server passwords such as Supermicro’s ADMIN/ ADMIN, and Dell’s root / calvin are long gone. In this article, we are going to discuss what has changed, why, and how it can impact your IT operations.
A Video Version
Most of our readers prefer our web articles, but this is a piece with less hardware and more discussion. We have a video version on YouTube if you prefer to listen instead.
Feel free to listen to that one instead of reading this article during your busy day. This article has fewer amazing high-end hardware photos than our normal review content.
Why Are Default Passwords Changing?
In 2018, California passed Senate Bill 327 or SB327. SB327 reads:
This bill, beginning on January 1, 2020, would require a manufacturer of a connected device, as those terms are defined, to equip the device with a reasonable security feature or features that are appropriate to the nature and function of the device, appropriate to the information it may collect, contain, or transmit, and designed to protect the device and any information contained therein from unauthorized access, destruction, use, modification, or disclosure, as specified. (Source: California SB327)
That is a fairly broad definition of what is needed. This law has made a sweeping change, specifically for server manufacturers. Although it does not apply to the OS, or software that is put on a server by a customer, it does apply to the BMC firmware and management interfaces. Specifically, server manufacturers are concerned with is this part of Title 1.81.26:
1798.91.04.b Subject to all of the requirements of subdivision (a), if a connected device is equipped with a means for authentication outside a local area network, it shall be deemed a reasonable security feature under subdivision (a) if either of the following requirements are met:
- The preprogrammed password is unique to each device manufactured.
- The device contains a security feature that requires a user to generate a new means of authentication before access is granted to the device for the first time.
(Source: California SB327)
Most server vendors are focused on complying with SB327 by meeting the first requirement. It seems as though AMI enabled a specific feature in its MegaRAC BMC software solution to help its customers comply with (1) which means we are seeing unique passwords. As a result, this year we are seeing the industry shift to randomized passwords. As a quick note, this is not necessarily unique. For example, HPE servers have had unique iLO passwords for generations. You can see the label HPE uses in this picture from our PCIe HPE ProLiant DL325 Gen10 Plus and DL385 Gen10 Plus first look.

Here you can see the label on the front right of the top sheet metal portion of the server.
Impacts on the Industry
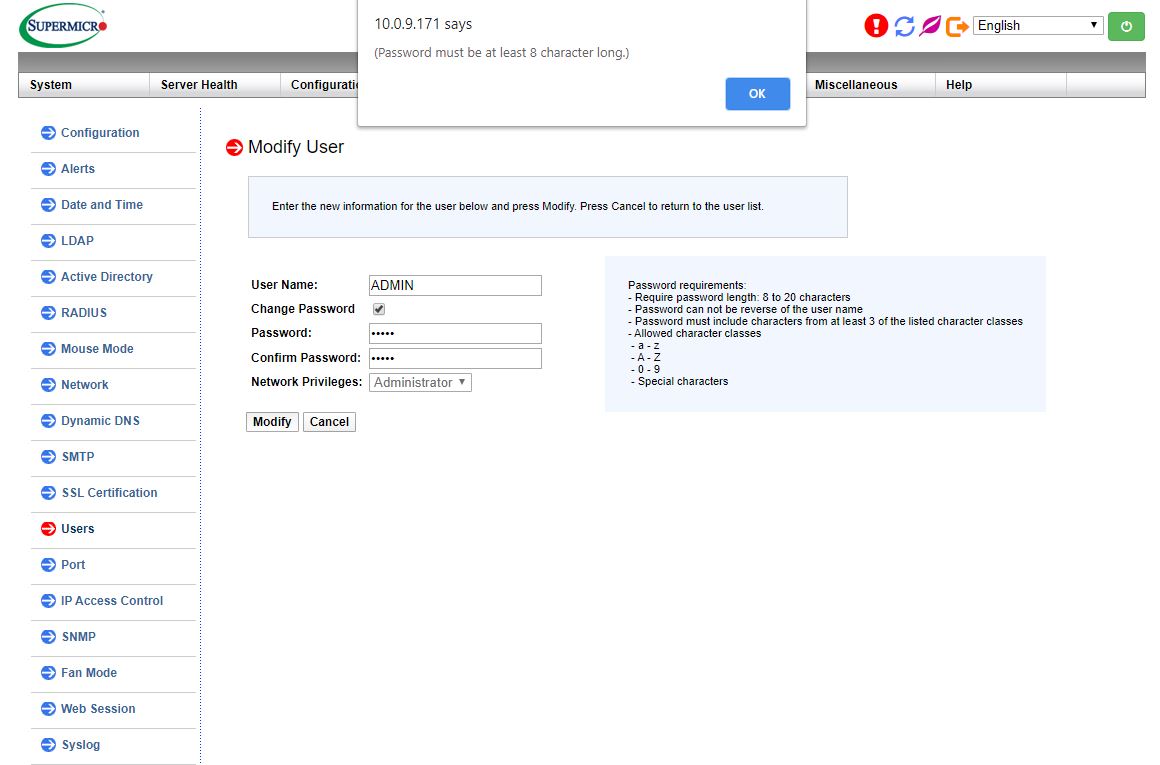
Perhaps one of the biggest changes is that we are seeing server buyers unable to login to their servers. For example, the test system for our Supermicro 2049P-TN8R Review still used the legacy Supermicro default password of ADMIN / ADMIN. Our Supermicro 2029UZ-TN20R25M Review saw a system that utilized the new unique password solution. The password is printed on the service tag:

We noted in that review that Supermicro needs to make this larger and easier to read. The password is generally printed next to the BMC MAC on Supermicro motherboards with the new labels. If you purchase a motherboard you will see a label on the CPU socket cover. The idea is that you can affix this label to the system or put it somewhere safe.
Supermicro is noting the new unique passwords on boxes of its BMC equipped products. This includes both servers as well as motherboards. Here is an example from an X11 motherboard we will have a review of shortly.
The company is putting them on their mainline server boxes as well with a small notation.
Other companies are following suit. We have seen MegaRAC based solutions from companies such as Gigabyte and ASRock Rack also adopt the new unique password model to comply with SB327.
Other segments are going to feel this pressure as well. For example, we saw a default Netgear password of “password” in our recent Netgear GS110EMX Review.

Netgear uses this default password with no username. When we did our Netgear MS510TX Review This Is One Funky Switch and harped on this fact, we received a lot of comments saying that default is not an issue:
We received that unit in 2019 but it seems like Netgear is focused on part 2 of the above SB327 test since its wizards direct a user to change passwords upon first access.
While this is a US State law, not even a US federal law, it has global implications. Vendors generally try to keep a consistent product portfolio in the US and globally. As a result, even systems shipped from outside California/ US to customers outside the US will see this change. Supermicro, for example, stated that it is keeping a global SKU stack even for systems shipped from Europe and Asia.
Operational Changes to Consider
The change has some fairly big operational impacts. A quick anecdotal example is what happened with that Supermicro 2029UZ-TN20R25M Review. We installed the system in racks saw, it booted, and left the data center expecting that our scripts would provision the system as normal. When we went to check on the system later, and access the IPMI/ management interface, something was off.
Our scripts were designed to use the default ADMIN / ADMIN for Supermicro servers. With the random default password set, we were stuck. We needed to go back to the data center to check the small service tag. Checking that small text overhead after hours when there is less light was very difficult.
After getting the default password, we attempted to use ipmitool to change the default ADMIN password. It turns out that in the version of firmware we were using, there was a password requirement that prevented us from changing the password to “ADMIN” so it could then go into our scripted workflow. We tried changing it via the WebGUI and saw the same issue. Due to the new password rules, one cannot change this to “ADMIN”.
There are two main ways around this. The first, is to use Supermicro’s ipmicfg feature. You can see that in Reset Supermicro IPMI Password to Default ipmicfg. It turns out, ipmicfg is better at setting Supermicro passwords than ipmitool. Supermicro also has python scripts that utilize Supermicro Update Manager (SUM) that can scan an IP range and set passwords to “ADMIN” or another value. For those python scripts to work you need the MAC addresses and unique passwords of each machine. If you have a handful of machines, it is not too bad. If you have many machines, you will certainly want to get this list through your sales point of contact to make provisioning easier. Another tip is that if you are using a reseller to purchase servers and the servers are not being sent to California, then asking the reseller to set a password may make sense.
There are many who welcome a randomized password default and will use systems as-is with it. There are others who will build other workflows around this new regime. Still, this is both a positive step for the industry as well as a potential pitfall for operations if one is not aware of it.
Final Words
There are many servers and IT products where SB327 will not have an impact. They were already using randomized default passwords. As the industry transitions, hopefully this becomes part of standard IT workflows. We are using Supermicro as an example here because they sell not just complete servers, but also motherboards. Purchasing a motherboard with a unique password and integrating it in a system will mean one needs to properly record and label the unique password so that one does not need to dive into the chassis to retrieve it later. For our VAR readers, this is both a consideration as well as a way in which you can help your customers.
One thing is for sure, as you prepare your next set of server, switch, and storage purchases, this is going to be a change for many in the ecosystem. Some, such as HPE ProLiant customers, will not see a difference. Others will repeat our steps of installing a system without noting the unique password and have to potentially go on-site to retrieve it. At STH, we prefer our readers to know about this changing landscape and adjust their operations accordingly.



I encountered this updated security provision about 2 years ago in a security NVR type of device.
The installation instructions provided with the product did not match the presentation on the screen even 1 bit.
The installation messages on the screen were more inscrutable than a fortune cookie proverb written in Latin.
I contacted the company’s tech support about the complete disconnect between the installation instructions and what I was seeing. I sent them screenshots of everything, including the misleading GUI from the product’s setup process. I told them the product was unusable in it’s current state since none of the system menus had yet to be presented. I asked for a resolution or my money back. That should be a simple choice for a company that is based in …
wait for it …
CALIFORNIA !! – Home of some of the most stringent consumer protection laws in the USA
Needless to say the company’s tech support staff never could figure out what their product was doing.
After some tinkering with the misbehaving device I determined that what it wanted me to do was “SET the administrative password for the device before I could use it”.
If that 1 instruction, “SET the Administrative Password”, had been provided in the installation instructions I would have known what to do and not had to hassle the company’s clueless tech support staff.
The imported (and what isn’t imported nowadays?) product had “support staff in the USA”, but they seemed to respond at odd hours or were only available specific times. After carefully examining the product I figured out what was happening; support calls forwarded overseas and support emails handled offshore.
My ten year old cable modem and external WiFi has the password sticker feature, there’s no reason everyone should have the same default password; in the IT world changing the password should be an expected requirement, but it’s sufficiently infrequent in the consumer sphere that breaking in would be easy.
As for the “admin” problem (too short), change your default to “admin1234”, and use a unique password that’s sufficiently strong. You are always going to have to look up something (pull open a book) because you should be changing your passwordS every few months and just prior to an employee leaving.
Wardriving is common enough that it’s worth changing your home’s WiFi password regularly, to send them to your neighbors who don’t.
This particular issue aside, why is the state even getting involved in this? Seems like a pretty large overreach.
Do you have a second source for this law? Bad reporting not to.
Are you like, dumb? It is literally on the CA Gov website:
https://leginfo.legislature.ca.gov/faces/billTextClient.xhtml?bill_id=201720180SB327
erwindalegrift – we do not second source enacted law which is a public and primary reference source. There is a big difference between second sourcing a rumor and stating a law that is currently in effect. I have a JD and in legal research and writing as a 1L something that was commonly taught was that you can (and should) cite recorded statute. You can interpret the meaning to a specific set of facts. In this case, SB327 is now law in California so we are not going to second source that.
Clearly, playing to the lowest common denominator, and, as clearly some admins were so negligent to leave commonplace/well-known default passwords/logins, clearly this new practice ought to take care of it….