Supermicro AS-1024US-TRT Block Diagram
Supermicro’s block diagram is basically done at two levels. The first is at the level of the Supermicro H12DSU-iN motherboard that is shared with this server along with other Supermicro designs.
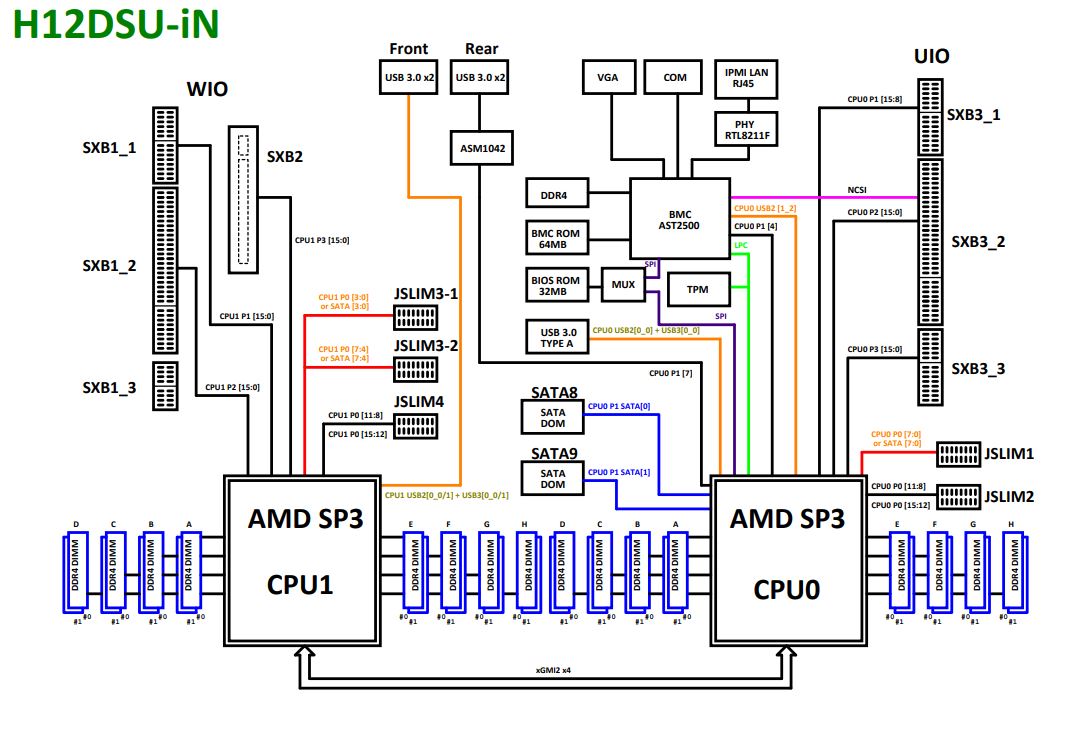
The second is at the system level which has a fairly high-level diagram. Here we can see a few important points:
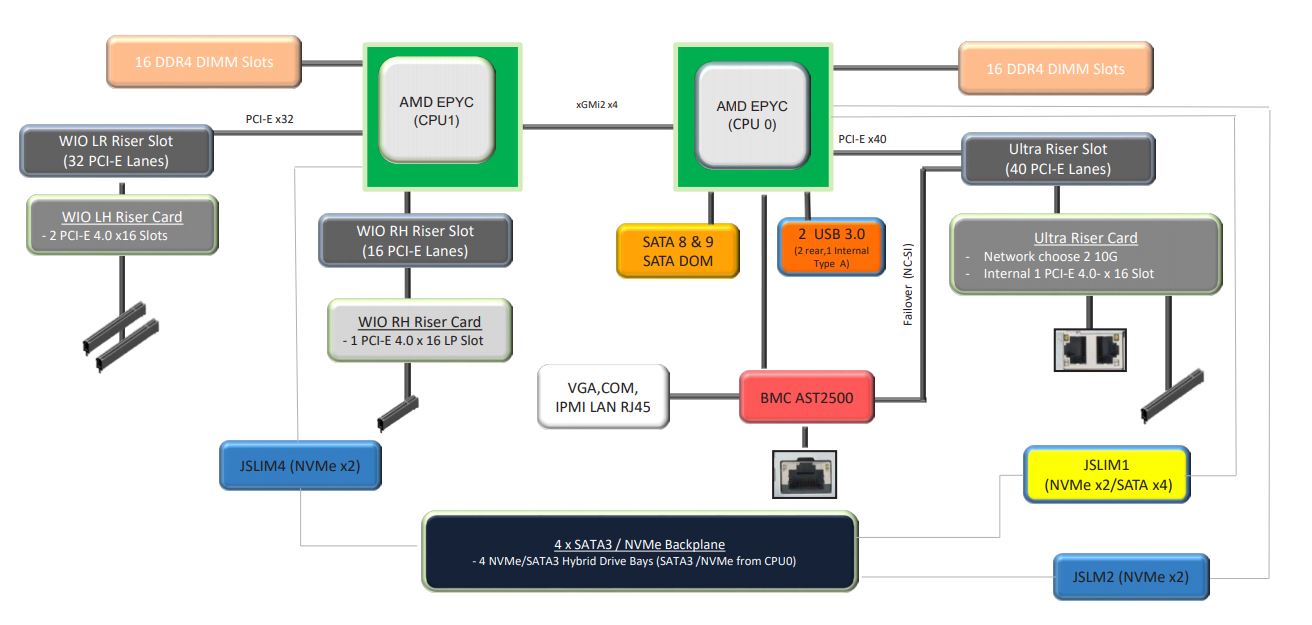
First, we can see that we need both CPUs installed to provide I/O connectivity to the full server and slots. Second, we can see that we have a full socket-to-socket link between the two processors. In a 1U system, having the 3x XGMI2 link configuration making 16x PCIe lanes available is less desirable since there is physically a limit to how much I/O one can fit into a 1U server. Dell’s motherboard in this 1U dual EPYC class, for example, has that flexibility, but in its 1U form factor, it is a cost adder without much if any practical benefit in the system.
Supermicro AS-1024US-TRT Management
These days, out-of-band management is a standard feature on servers. Supermicro offers an industry-standard solution for traditional management, including a WebGUI. This is based on the ASPEED AST2500 solution, a leader in the BMC field. The company is also supporting the Redfish management standard. Something that we wanted to highlight is that the password has changed.
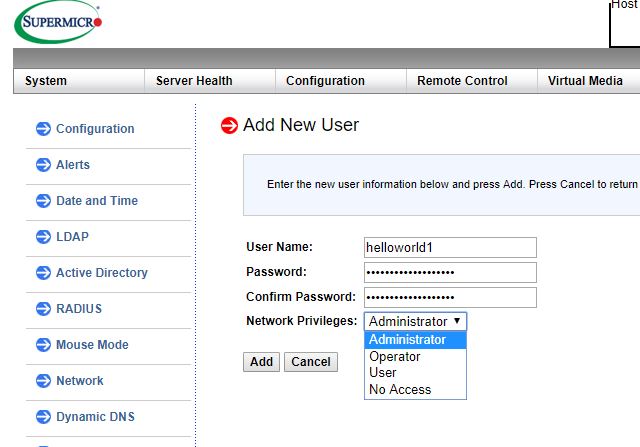
Our system had the unique password solution built-in. This is mandatory on new servers due to legal requirements. For a quick overview of why Supermicro and the rest of the industry are moving to unique BMC passwords, you can see Why Your Favorite Default Passwords Are Changing and the accompanying video:
On this server, we see similar features as we would across the Supermicro A2/X11/H12 ranges. That means whether you are using an embedded Intel motherboard or a 4U Intel Xeon or AMD EPYC storage server, you will have a similar look and feel to the management experience.
In the latest generation of Supermicro IPMI is an HTML5 iKVM. One no longer needs to use a Java console to get remote KVM access to their server.
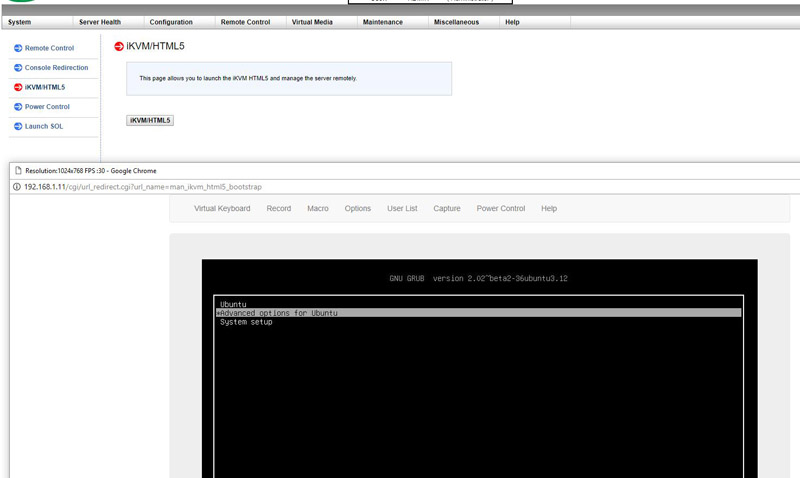
Currently, Supermicro allows users to utilize Serial-over-LAN, Java or HTML5 consoles from before a system is turned on, all the way into the OS. Other vendors such as HPE, Dell EMC, and Lenovo charge an additional license upgrade for this capability (among others with their higher license levels.) That is an extremely popular feature. One can also perform BIOS updates using the Web GUI and even do simple tasks such as power cycling the server.
This pricing differential for a serviceable iKVM functionality is a big deal in this segment. Adding a $200 license to a server can add 10% or more in the embedded platform costs. Supermicro’s iKVM feature is extremely popular due to its inclusion with the server.
Next, we are going to discuss performance.




I wish STH could review every server. We use 2U servers but I learned so much here and now I know why it’s applicable to the 2U ultras and Intel servers.
Hi Patrick, does AMD have a QuickAssist counterpart in any of their SKUs? Is Intel still iterating it with Ice Lake Xeon?
I’m fascinated by these SATA DOMs. I only ever see them mentioned by you here on STH, but every time I look for them the offerings are so sparse that I wonder what’s going on. Since I never see them or hear about them, and Newegg offers only a single-digit number of products (with no recognition of SATA DOM in their search filters), I’m confused about their status. Are they going away? Why doesn’t anyone make them? All I see are Supermicro branded SATA DOMs, where a 32 GB costs $70 and a 64 GB costs $100. Their prices are strange in being so much higher per GB than I’m used to seeing for SSDs, especially for SATA.
@Jon Duarte I feel like the SATA DOM form factor has been superseded by the M.2 form factor. M.2 is much more widely supported, gives you a much wider variety of drive options, is the same low power if you use SATA (or is faster if you use PCIe), and it doesn’t take up much more space on the motherboard.
On another note, can someone explain to me why modern servers have the PCIe cable headers near the rear of the motherboard then run a long cable to the front drive bays instead of just having the header on the front edge of the motherboard and using short cables to reach the front drive bays? When I look at modern servers I see a mess of long PCIe cables stretching across the entire case and wonder why the designers didn’t try avoid that with a better motherboard layout.
Chris S: It’s easier to get good signal integrity through a cable than through PCB traces, which is more important with PCIe 4, so if you need a cable might as well connect it as close to the socket as possible. Also, lanes are easier to route to their side of the socket, so sometimes connecting the “wrong” lanes might mean having to add more layers to route across the socket.
@Joe Duarte the problem with the SATA DOMs is that they’re expensive, slow because they’re DRAM-less, and made by a single vendor for a single vendor.
Usually if you want to go the embedded storage route you can order a SM machine with a M2 riser card and 2x drives.
I personally just waste 2x 2.5” slots on boot drives because all the other options require downtime to swap.
@Patrick
Same here on the 2×2.5″ bays. Tried out the Dell BOSS cards a few years ago and downtime servicing is a non-starter for boot drives.
I should maybe add that Windows server and (enterprise) desktop can be set to verify any executable on load against checksums, which finds a use for full size SD cards for my shop (and greatly restricts choice of laptops). the caveat with this is that the write protection of a SD card slot depends on the driver and defaults to physical access equals game over. So we put our checksums on a Sony optical WORM cartridge accessible exclusively over a manually locked down vLAN.
(probably more admins should get familiar with the object level security of NT that lets you implement absolutely granular permissions such as a particular dll may only talk to services and services to endpoints inside defined group policies.the reason why few go so far is highly probably the extreme overhead involved with making any changes to such a system, but this seems like just the right amount of paranoia to me)