Fortinet has a new ASIC for edge appliances. The Fortinet FortiSP5 integrates security functions on a 7nm chip for its next-gen appliances. We have not covered Fortinet in some time, but since we have been focusing more on the networking space over the past few quarters we figured why not cover this chip as well.
Fortinet FortiSP5 ASIC Launched
The FortiSP5 has a built-in Layer 7 firewall and acceleration for a number of other features. For example, it is able to power up to 37Gbps of IPsec VPN and 40Gbps of firewall traffic.
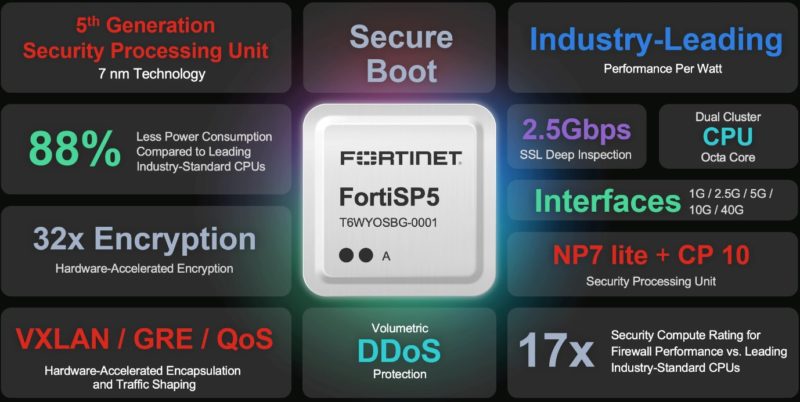
There are a few interesting specs on the new chip. First, the chip supports 2.5Gbps of SSL deep inspection, volumetric DDoS protection, and 2.8Gbps of threat protection. There are other features like hardware-accelerated QoS and VXLAN/GRE hardware encapsulation that make a lot of sense on a chip like this. Likewise, Fortinet appliances are designed to run the company’s own software (e.g. FortiOS), so having a secure boot feature that validates that a valid OS is booted makes a lot of sense.
Some of the specs are a bit strange. For example, it has 88% lower power consumption compared to “Leading Industry-Standard CPUs.” No citation is given on what is an industry-standard CPU. Is it an Intel Xeon Platinum 8490H with 800Gbps of QAT acceleration? Is it a Marvell Octeon 10 that we looked at a few months ago? Perhaps it is an Intel Xeon D-1700/ D-2700 that we looked at the OpenSSL and IPsec VPN offload features of a few months ago.
Fortinet makes a similar claim about next-gen firewall (NGFW) performance saying that FortiSP5 is 3.5x faster than “leading standard CPUs”. The 32x faster encryption performance versus something that was not defined.
These days it is fairly uncommon to see vendors not at least footnote the comparison point. We hope that Fortinet at least starts to provide citations for what it is using to make claims in the future.
Final Words
For a company like Fortinet, it makes a lot of sense to have a more specialized ASIC with more networking and accelerator technologies. The FortiSP5 is the next generation of the company’s architecture, and it is great to see it is finding enough performance differentiation to build an ASIC. We have been discussing acceleration in both our CPU series and DPU series on STH. These types of edge gateway appliances are certainly a use case that can make use of heavy acceleration so it makes sense.

Perhaps the bigger question is: should we start looking at Fortinet boxes. Above was a Fortinet FG-60C that STH was looking at deploying in its data center lab in 2013. I need to get the story of why STH did not at the time. As we have looked at a lot of hardware solutions for open-source and those like the Netgate 4100 pfSense Plus router-firewall-VPN appliance, perhaps it is time to add this class of device to the mix.





Since Fortinet uses all sorts of obfuscated metrics I don’t think it makes sense to benchmark the unit in itself. The more interesting bit would be to compare performances with equal feature sets (IPS, VPN, IMIX etc.) to demonstrate real world utilization.
Ditto what David said. Seeing how a Fortigate 100F or its upcoming G-series equivalent compares to a Netgate 8200 would be interesting. That would be a lot of work though and worthy of a series of articles. There are so many pieces to the Fortinet ecosystem that you could play with.
I’d like to see STH do its normal breakdown.
We’ll be deploying hundreds of Fortigate units in Europe the coming two years for a veterinary company. I’d be very interested in a review and technical breakdown of Fortigate units and services.
I use Fortigate extensively and have for decades.
The lots of blather and no substance on marketing is very indicative. For the price point they are a good option I suppose. But if you have money go somewhere else.
The support is horrible on the best days and you will need to call them as their stuff breaks a lot. I think their support is just homeless bums they recruited off the street that day on the way into the office.
They also are clearly hardware company. Do not buy their virtual appliance, do not buy anything from them except the firewall and the log collector for it.
Chuck may be a little harsh on them, but in general it’s true. Fortinet is great for FortiGate (FW) and FortiWiFi (FW + integrated AP), and for both I’d say ideal for SOHO and small business units. We’ve used hundreds in as many small locations and I love them for simplicity and user friendly UI. We’ve used bigger units in HQ, and they are great for offices and as central point to concentrate all those hundreds of VPNs for smaller devices. But I’d never place one again in even the smallest datacentar. Lab – yes, home lab – perfect, central or branch office – natural fit. DC? Never! Not that we haven’t tried…
I still love them very much, they have their peculiarities, but they’re very manageable. Yet still, not for the big league.
I’ve used Fortigates at home for years, and just dropped support on my 61E. Support contract costs have been rising, such that you don’t get more for your money as they introduce new models. Fortinet also has a habit of using their user base to beta test software revisions – you should not expect a new product to function until it’s seen a few. As for testing, I would be interested in some third-party metrics as well, just as data points. Fortinet’s marketing is aimed toward… well, suckers, but the performance figures in their data sheets are usually pretty accurate (as were Netscreen’s back in the day). You just need to understand what they say and do not say.
I’d be interested in firewall testing, but that’s a big (and expensive) thing to get into, especially if looking at the NGFW/ “layer 7” capabilities.
We looked at Fortigate when we were shopping for a new NGFW, and ended up passing them up because while they do provide numbers for how fast things can run, that’s only if just that particular feature is enabled. Turn on SSL inspection, IP sec firewall, and threat protection all at once, and you’re looking at significantly lower performance from a given unit. So you have to buy one (or several) tiers higher model, and the cost advantage isn’t as great.
We ended up going with Palo Alto, since the numbers they rate are with everything turned on. I know those (for the generations we have) use Marvell Octeons for the smaller units, and Octeon (data plane) + Xeon (management plane) + FPGA for the higher end models.
If STH were to do a Fortigate review in depth, it should probably include Palo Alto as well.
OPNsense/PFsense/Netgate performance is pretty well understood, but are their detection, management and performance as capable as the PA, Forti, Juniper SRX, Cisco ASA, Meraki’s?
Firewall’s are more than just the performance metrics of how much bandwidth they can push.
Honestly we’ve even got TZ400’s out there that are running well under their rated capabilities because we’ve turned on DPI-SSL, CF, and so much logging that they bog down to <100mbps throughput. (not that Sonicwalls are great)
I think most sysadmins are more concerned with the security of these devices. Feature set is far more important than the headline throughput numbers on SSL, if it doesn't support the features you need, who cares how fast it can push those packets. Bandwidth is just a price point in firewalls, features define the real value.
I’ve deployed thousands of FortiGates over the last 2 decades so have good insight into areas like performance, feature set and support. And practicality. Some here have indicated some negatives and yes there are (which vendor doesn’t have?), but on the whole there’s little else in the market that compares when looking at the solution holistically.
1. ignore the marketing no’s and just size your boxes correctly; FortiGates perform above anything else on the market at the same price point. I’ve seldom been afraid to switch on all features on even the smallest of units (E and F gen). Memory sizing in certain models can be a problem, but as I said size properly and no issue
2. FortiGate provides double the performance of Palo Alto (I’d suggest they are Fortinet’s closest competitor) at the same price point; I rate PA’s app control slightly ahead of FGT’s but is the price differential worth it? And some PAs (especially older models) would die with certain features turned on
3. we’ve used FGTs in everything from mom and pop shops all the way up to enterprise, datacenters and the largest ISPs. They perform, are feature rich and they’re stable (as long as you practice proper firmware lifecycle management). Not much can match a 3xxx-series unit these days i.t.o. of performance and features. There’s little else I would trust to run 40- and 100Gbps segment-based protection.
4. FGT’s security set has been bulletproof (i.t.o. security) over the last period. Their threat research is amongst the best in the world and they also initiated CTA which provides for even more threat feeds. As long as you have DPI switched on (many don’t for some reason), FGT’s threat ID is amongst the best available
5. The network stack on the FGT is unparalleled – everything from hard and soft switches, aggs, wire pairs and mirroring/span, to VXlan, IPsec and eMAC. Then of course there’s the built in switch and AP controllers, VDOMs, etc.
6. no per user pricing on the box itself – you want 10k users on a 40F? go for it – won’t work very well but there’s no licensing limitations to stop you from trying. Contract/renewals/subs pricing remains very good in comparison with the competition …
7. yes FGT’s software QA can be dicky at times but that’s where proper firmware lifecycle management comes into play – we’ve never had an issue where there are show stoppers due to running a .0 release. Others (and no offense here) have difficulty understanding the concept of business continuity vs “let’s play with the latest feature release on a business critical firewall”.
8. Fortinet have the widest portfolio of security products out of any vendor on the market – it’s then a pity that many folk only look at the FGT; the real power of Fortinet’s ecosystem is their security fabric and integration between products; I love being able to redirect traffic from an FGT to FWB for waf protection (as an example) with a couple of clicks. Or push tags from EMS/FCT to FGT so I can control traffic based on endpoint posture status. And so on. FMG and FAZ are great LMRs and managers-of-managers (once you get past the quirks).
9. Fortinet’s support seems to vary wildly depending on where you are in the world. I know that they make use of distie support in certain jurisdictions and this could be why. But the best option is to lean on your account manager and make sure that your issues (technical or not) are sorted out. Maybe we’ve been lucky with out interactions with support, but on the whole I’d give it a reasonable 7/10
This probably sounds like a fanboy report but I genuinely look at things holistically and from a business p.o.v. If PA could sort out their pricing, then they’d be at the top of the heap but I can’t justify significant price deltas for only a little improvement. Cisco’s stuff is 10 years behind PA and Fnet. Checkpoint/Nokia is decent although their UI is dicky and it’s only commit-based policy mechanism. Sophos, S/wall and Barracuda aren’t enterprise capable …
So that’s my 3 cents
I hope this silicon from Fortinet is not gimped again by lack of buffer & I/O support. Prior generations cannot approach real throughput targets in real world usage, especially SD-WAN implementations. The buffers and subsequently chips could not handle the encryption per stream and would cause entire WAN geos to just fall over. From what I’ve seen, a 32x encryption speed increase is closer to the minimum of what they needed for this generation.
These “industry-standard CPUs” could all drastically outperform Fortinet gear because they had RAM and could generate the keys much faster.
With all of this said…
This looks to be a mostly off-the-shelf ARM CPU with common interfaces.
Probably a gently incremented Mediatek Filogic 880 via Mediatek’s custom ASIC group.
Fortinet won’t let you. They don’t like independent stuff like STH. They’ve got a control issue.
They’re actually good boxes, with amazing performance for the price, easy to configure, though can also get very complex with them. I have maybe RMAd three of the 1000+ I have deployed in the past ten years. Support not great, but usually call just to find out I fat fingered something, just gotta stay on their mainstream firmware releases unless you like memory leaks. “Security Fabric” is awesome if you use their other products, but switch line is overpriced and lacking in 10gb+ ports
My 16 years worth of experience deploying and maintaining Fortinet firewalls, mirrors what Robby said.
They’ve been very reliable, ultra fast (high bandwidth and low latency), feature rich and give excellent coverage against malicious traffic.
Very rarely have I needed to contact support, so I can’t claim great insights on that front.
On the point Guy mentioned about performance dropping as you enable more and more features, this point applies to ALL firewall products from ALL vendors, however the irony here is that this effect is seen the least severely in Fortigate firewalls which are ASIC accelerated, which these days are ALL of them minus the VM offerings of course.
For those who claim that Fortinet firewalls are not for the enterprise, they might like to take a stroll through a major datacenter of the calibre which hosts the likes of Google, AWS, Apple, Facebook, etc. Because whenever I do so, it’s a case of, “Is that white box a… yes it is. Another Fortigate”.
Fortigate firewalls are used at every level and I know of ISP and cloud providers who use them to provide ASIC accelerated “virtual” (hardware) firewalls to their customers via Fortinet’s VDOM feature.
Palo Alto are neck and neck with Fortinet for features, but the value is not there for performance/price.
Another thing I’ve found with Fortinet when stress testing Fortigate units, is that Fortinet tends to under-promise and over-deliver. They’ve always been able to pass more traffic for each feature than their glossy brochures claim.
I’ve pushed Fortigate firewalls till I’ve found individual fail-closed / fail-open points for their security features, including (with some units) to wire-speed saturation with the most stressful 64 byte ethernet frames, using Spirent stress testers. The Fortigate’s stay up, remain responsive to network traffic and merely fail open or closed for specific features, which was configurable.
When I’ve attempted such extreme stress testing against firewalls from other brands, I’ve managed to cause them to become completely unresponsive and then abend. The good ones then reboot when their watchdog timer is no longer being tickled, but the lesser firewalls just stay dead until a power cycle.
I can’t speak highly enough of Fortigate firewalls.
The G series launched recently (90G/91G), but seems same SP5 chips. Been a fan of Fortigates for many years implementing and maintaining a number of them across numerous clients. They are fit-for-purpose hardware, make sure to fit them correctly :)