Today we have news of a new set of security vulnerabilities that allegedly impact AMD EPYC and Ryzen CPUs. Every single silicon CPU has had some bug or vulnerability so frankly, this is of little surprise. As security research teams scramble to find these bugs, standard industry practice is that 90 days are given to vendors to mitigate the risks so that millions of compute nodes are not compromised immediately. Even sharing what the issues are can give enough detail to lead to issues in the field. These vulnerabilities were disclosed 24 hours after being brought to AMD, and the whole setup looks beyond bizarre.
About the AMD EPYC and Ryzen Vulnerabilities
Here is the video posted about the vulnerabilities via AMDFlaws.com and YouTube.
Essentially, these vulnerabilities allow unauthorized parties to launch persistent attacks on the machine. They may very well be real, but as we are about to see, CTS/CTS-Labs/CTSLabs is unwilling to state, as a fact that they are real.
Why this Looks Bizarre
There are quite a few items here that look truly strange. As we watched the Interview videos, as an example, the production quality was good, including the VP of R&D at 1:44 giving an interview in a data center. As you can see, that is a green screen background. Anyone in the industry knows that if you give an interview in the data center, you are going to hear cooling systems like fans or you are not really in a data center. Many production crews know this, and when catering to technical crowds, they take this fact into account. Here is the interview video:
https://youtu.be/pgYhOwikuGQ?t=1m44s
What gets even stranger is the last few seconds of the logo screen:

The company on the AMDFlaws site purports to be “CTS-Labs”, not “CTSlabs”, note the “-L”:
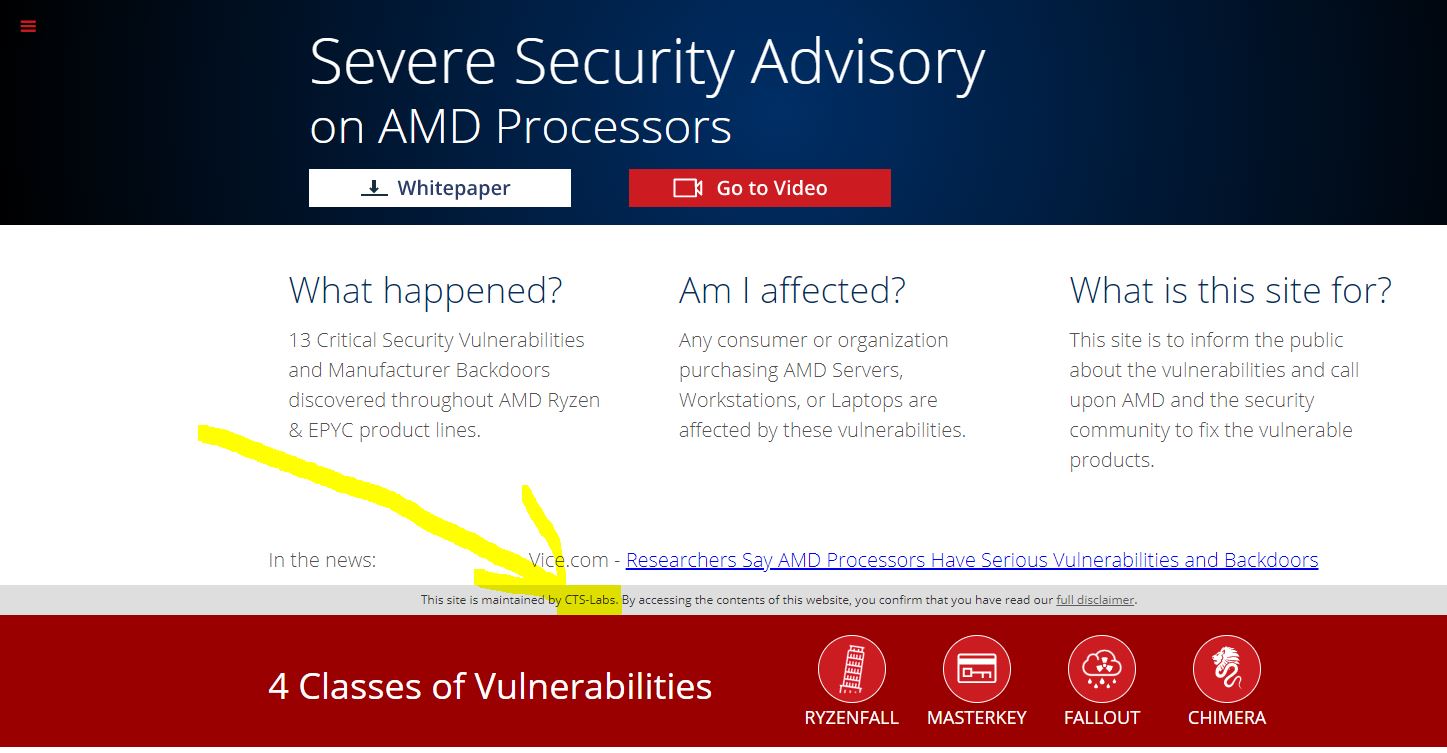
As someone who has a JD, MBA, and is involved with publishing, the next step, was to look at the full disclaimer. This is usually the legal portion drafted by attorneys who care about things like entity names:
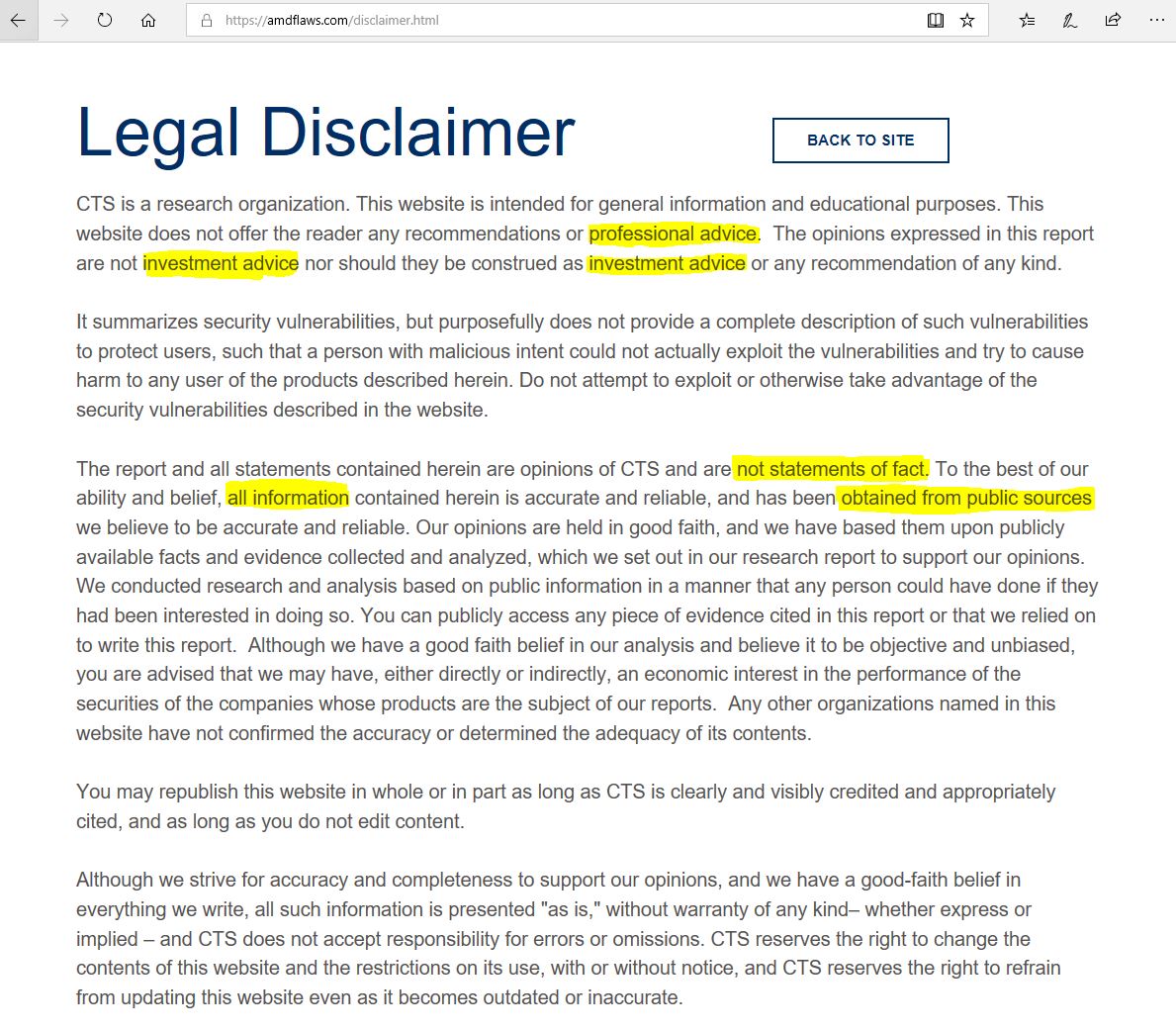
Where to begin. First, normally when you abbreviate a legal name, you would put CTS-Labs (“CTS”) before just using CTS throughout the document. That was a must-do when I passed legal research and writing my first semester in law school. We now have three potential entity names “CTS” from the “Legal Disclaimer”, “CTS-Labs” from the “company’s” website and AMDFlaws.com, and “CTSlabs” from the video. If you are reasonably careful, it is difficult to miss three times including in your legal disclosure document.
Anyone that puts “professional advice” and “investment advice” first is usually part of the investment community or a company that has to deal with SEC regulation. This is most likely drafted by someone who has seen these terms a lot but did not get trained in legal writing (see the paragraph above.)
The third paragraph gets scary. “The report and all statements contained herein are opinions of CTS and are not statements of fact.” [Emphasis added.] Essentially, CTS does not believe what it reported is fact. We do not know about CTS-Labs or CTSlabs view on whether they think it is a fact. Beyond that, “all information” was “obtained from public sources.” That is a little strange. It looks a far cry from a professional disclosure.
We took the next step to look up CTS-Labs’ website and saw something shocking before immediately closing. It is not even hosted on HTTPS. Everyone may have opinions about how secure HTTPS is, but if you cannot setup a HTTPS website for your security research firm, we are not sure how “[w]e work with hardware manufacturers to design, implement, and deploy high-security solutions…” can be accurate. You would think that step 1 in demonstrating you can design, implement, and deploy high-security solutions
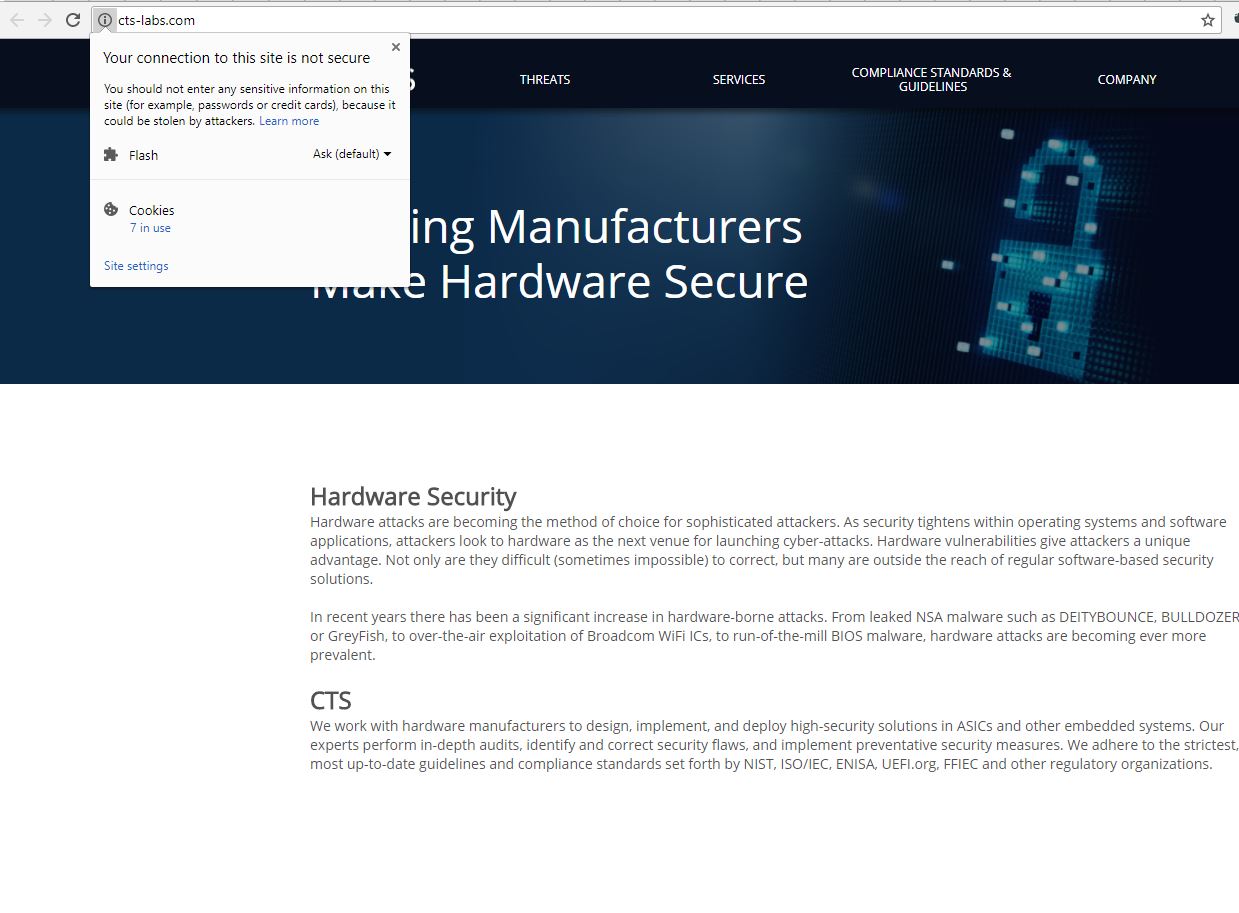
In summary, whatever entity this is, got the information ostensibly from public sources research done by others, which contradicts what they seem to be saying in the video. They are also saying that their statements that there is a vulnerability are not statements of fact.
AMD’s Response
We reached out to AMD as this seems extremely strange. Here is the response we received from AMD:
At AMD, security is a top priority and we are continually working to ensure the safety of our users as new risks arise. We are investigating this report, which we just received, to understand the methodology and merit of the findings.
In context here for those who have not worked at a big corporation, every large company takes some time to assemble resources. If your security policy is looking to react within 90 days, having under 24 hours usually will not provide time to even get the right people together to start validating the claim. With Spectre and Meltdown, it took Google coming to Intel and other large players and a coordinated effort over months to address the issue, and there are still bits not finished.
Final Words
If you are tallying the bizarre, we have:
- An alleged security firm that cannot secure its domain with HTTPS that
- Is not sure what its legal entity name is
- Whose methods relied upon public information stated that
- The vulnerabilities they are talking about are not factual and
- Were disclosed publicly in 24 hours instead of the standard 90 days
Then the question of who could be behind this comes into play. The production quality on video seems to be decent and there is a good amount of content. I have gotten several pings, and I frankly would be shocked if this was Intel. It would not be how I would expect them to compete and the legal disclaimer is too sloppy to be Intel.
While we do not know exactly who this is, best guess, the SEC will be looking into groups of short sellers as it seems like a higher-dollar scare tactic akin to a pump and dump on a Bitcoin/ alt-coin forum rather than an actual security vulnerability disclosure.
There may, indeed, be a set of vulnerabilities with AMD EPYC and Ryzen. In fact, in all likelihood, there are undiscovered bugs and vulnerabilities as we see in any chip design from any modern vendor.
The key takeaway here is likely something that a partner at a large consulting firm taught me when I was just out of school trying to get him to look at the substance of a slide I made:
“If your presentation looks sloppy, people will look at you like you are sloppy and disregard anything you have done.”
For the sake of the computer hardware and security industry, we need to ensure that if this is a legitimate disclosure, that it is indeed put through a proper disclosure process.




Better buy AMD stock than paying attention to this financial scam. Would have expected more from STH
Did you read the article Alexander? It clearly disseminates the available information and presents it as a probable scam.
Wow that’s tough journalism. Alexander did you even read? This is one of the best investigations out there on the subject.
Alexander Your a Dumb ass!
Forgot good article.
Really nice analysis. I read about this in many other respectable sites, no one else mentioned the thing about the inconsistency of the name nor about the sloppiness of the disclaimer.
Good one Patrick. Traders to jail for this
It’s sad to see statements like
“Anyone in the industry knows that if you give an interview in the data center, you are going to hear cooling systems like fans or you are not really in a data center.”
The author clearly doesn’t have a lot of experience at various data centers. Equinix Ashburn and Sydney both have fishbowl conference rooms with good views of the DC, and even a quick Google of “data center conference room” shows several other images. It is also a thing at some companies for server rooms to be glass-walled, or at least have large windows, to show off the equipment. The noise is inside the equipment area and it isn’t that hard to find a real place to stage something like this, if you wanted to shoot in front of real gear.
Making a statement such as “it appears to have been shot in front of a green screen” could have stood on its own. Justifying that with a laughably false statement only detracts from the article.
https://amdflaws.com/disclaimer.html
“you are advised that we may have, either directly or indirectly, an economic interest in the performance of the securities of the companies whose products are the subject of our reports”
Nice.
PCWorld’s coverage states, “All [the vulnerabilities] would require a program running with local access and administrator privileges to exploit them.”
With Patrick’s analysis, I think we can dismiss this nonsense.
Will point my nephew to this, he does criminal investigative research for an attorney general’s office.
Oh, and I think we can dismiss the comments by the trolls above. (Patrick, see if you can get the IP addresses from the web logs of these imposters… I mean, posters. Point you right to these CTS scammers.)
Hi JG – I have been in plenty of DC conference rooms (I am in one in the Silicon Valley typing this.) The perspective used of in-aisle is not something that you can get in these conference rooms.
Better stated, not only have I been in such conference rooms, I have been with folks filming and trying to get that perspective.
Hi Patrick,
The guys at reddit found out that the backgrounds on the videos are shutterstock photos. Also, the domain of the website can be found on cacjed wrb pages, whete it says “SoM3 H4ck3r was here”. So much about security experts! All this info is from AMD reddit
Also, it appears that the Threadripper is not affected by these flaws, as it is never mentioned in the report
I’m in the category of folks who have been doing this for decades, and have seen data centers or machine rooms where an aisle (or aisles) butt up against windows, sometimes adjacent to the ops office or a conference room. You can definitely get views like that, though you might have to shop around awhile.
Given this fact, the statement you made was somewhat jarring.
You made a fair and fine point that this was a green-screen affair, it seemed pretty obvious, so the inclusion of the statement I’m questioning was unnecessary and detracted from the quality of the article for those of us who have seen counterexamples to the claim that was made. This doesn’t make the video any less phony, of course. The related “disclosure” and the rest of the analysis of it seemed well done.
The whole video is in front of a green screen.
https://www.reddit.com/r/Amd/comments/846gpm/how_cts_labs_created_their_offices_out_of_thin_air/