QNAP released a number of vulnerabilities today. What is interesting about these is that the build dates are from December 22 and 23 2021 and they are just hitting the security advisory list today January 1, 2022. That is about three weeks late. Given that, we wanted to point out two features one can use to get the newest builds and effectively do the mitigations that QNAP is disclosing.
Mitigating Today’s and Future Vulnerabilities
We are going to post the vulnerability information below. With two high and one medium vulnerability, and two of them are covering multiple CVEs, QNAP’s suggested course of action is to update to the latest version or at least a newer version.
As a result, one can do two things to mitigate these in the future. Turn on firmware auto-updates and turn on app auto-updates.
Turn on Firmware Auto-Update
The firmware auto-updating one may be a bit more controversial since there are reasons users will not update NAS firmware regularly. For many that just use the NAS as a store for files when they are working, this is likely something that you would want to do.
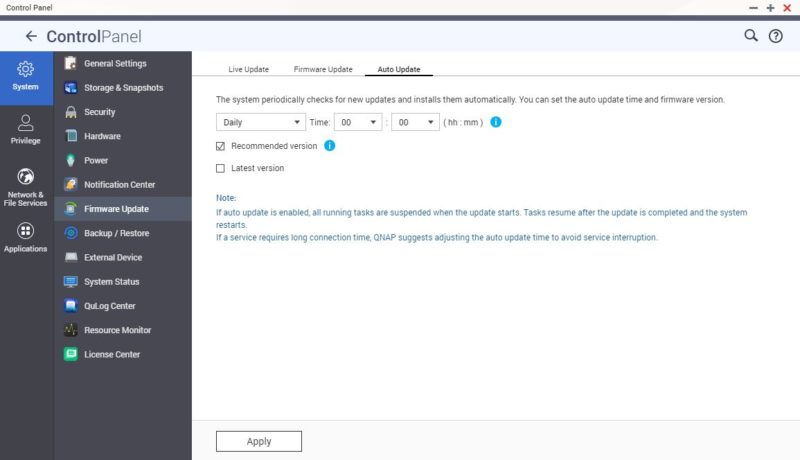
Here you can go to the Control Panel -> System -> Firmware Update -> Auto Update and have the system install new firmware automatically.
Turn on App Auto-Update
On the two vulnerabilities for QNAP apps, the above setting will not auto-update. Instead, one must go to the AppCenter and turn on Auto Update there.
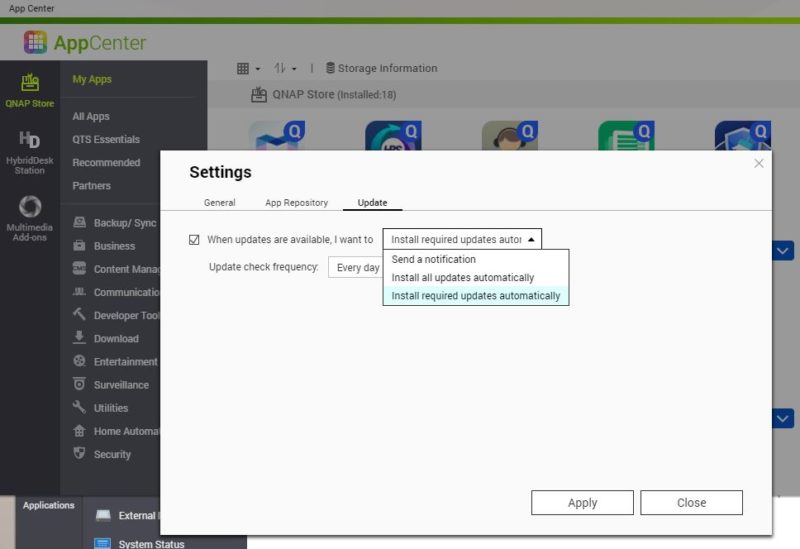
Here you go AppCenter then hit the settings gear on the top right and go to Update. There you can set an update frequency and choose to install every update or only recommended ones.
Set Update Notifications
For both of these, you can also set a notification. Many QNAP users do not know this, but QNAP has a very easy method to send notifications for events, including updates. Here is the notification for firmware updates:
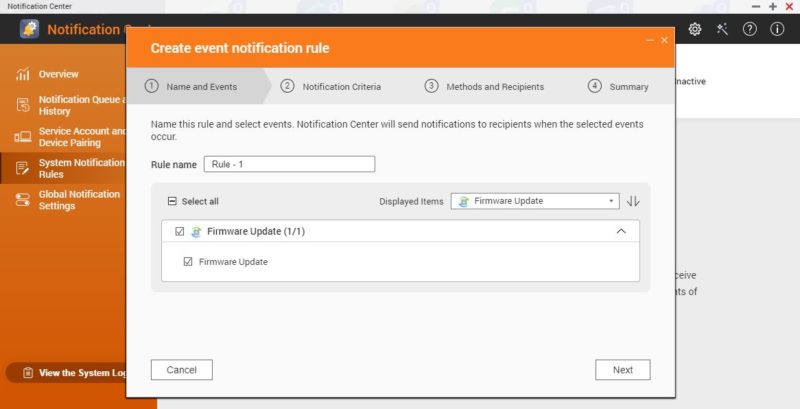
Here is the start of the app update notification flow:
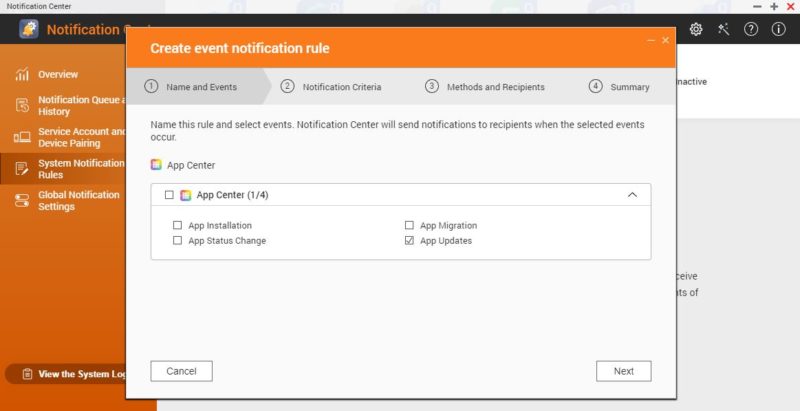
You can even turn on e-mail and integrate with services like Twilio and send SMS messages when there is an update available.
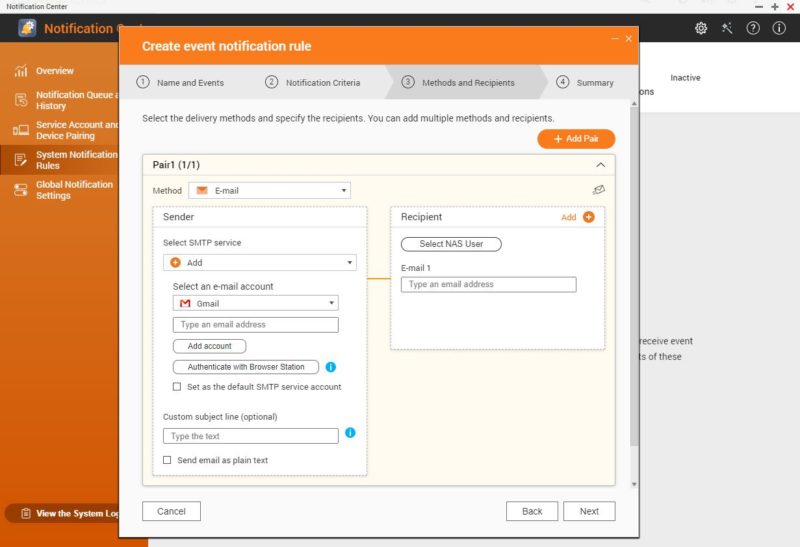
That example uses Gmail, but there are other options in the flow as well. You can also send the notification to multiple targets.
Final Words
It would be nice if the update to vulnerability timing was shorter. For users that need a reason to update, something like having two high-risk fixes and one medium in a new version would be a good reason to hit the update button. Still, we just wanted to show that there is actually a lot of functionality one can use to protect themselves. This is similar to what we recently showed in Secure Your QNAP NAS Immediately From Latest Wave of Attacks. These NAS units have a lot of features, but they often need to be implemented by users.
Vulnerabilities listed below.
The Three QNAP Vulnerabilities Disclosed 2022-01-13
Here are the three vulnerabilities:
ID QSA-21-57 (Source: link)
A vulnerability has been reported to affect QTS 4.5.3 and later versions, and QuTS hero h4.5.3 and later versions. If exploited, the vulnerability allows attackers to run arbitrary code in the system.
We have already fixed the vulnerability in the following versions of QTS and QuTS hero:
- QTS 5.0.0.1891 build 20211221 and later
- QTS 4.5.4.1892 build 20211223 and later
- QuTS hero h5.0.0.1892 build 20211222 and later
ID QSA-21-59 (Source: link)
A stack buffer overflow vulnerability has been reported to affect QNAP NAS running QVR Elite, QVR Pro, and QVR Guard. If exploited, this vulnerability allows attackers to execute arbitrary code.
We have already fixed this vulnerability in the following versions:
- QVR Elite 2.1.4.0 (2021/12/06) and later
- QVR Pro 2.1.3.0 (2021/12/06) and later
- QVR Guard 2.1.3.0 (2021/12/06) and later
ID QSA-21-60 (Source: link)
A cross-site scripting (XSS) vulnerability and an open redirect vulnerability have been reported to affect QNAP NAS running QcalAgent. If exploited, the vulnerabilities allow attackers to inject malicious code and redirect users to an untrusted site that contains malware.
We have already fixed these vulnerabilities in the following versions of QcalAgent:
- QcalAgent 1.1.7 and later





Automatic updates are the cure for all of the problems in life?
Gee…what could go wrong?
Perhaps you should ask people that downloaded the latest Microsoft updates for their servers (KB5009557 for Server 2019 and KB5009555 for Server 2022)…and then experienced system reboots every few minutes on their domain controllers. And Microsoft’s solution is to back out those updates…if you can. There are reports that those updates cannot be reversed on some systems; OS prevents it. Or if you can reverse those updates it damages other portions of the OS.
Ok, that is a Microsoft environment…and it never happens to Linux, right? I doubt it. I seem to remember a first release of Linux kernel 5.10 borking systems with Nvidia graphics cars; I suffered through that one myself.
So, what can go wrong by turning on “fire & forget” automatic updates? Lots of things.
I would say this: Stick with notifications of available updates. Then get in the habit of not ignoring those emails. Read and carefully consider those updates. Test them if you can on a “test system” before deploying them to a “production system”.
And for gosh-sakes people…be careful with how these NAS systems are accessed. Lock stuff down. Does it really have to be accessible over the Internet? Questions & considerations like that are very important and routinely overlooked by inexperienced, overworked, or bullied (by the bosses) admin folks.
But automatic updates? Ba-waa-hahaha!
It’s the lesser of evils tho sleepy. For 99% of people using these NASes auto update is better than no update. Not everyone has a test and a production QNAP. I’d bet they mostly sell like 2 or 4 bay NAS where there’s 1 in the office. I’d rather chance an autoupdate that’s been vendor tested than just leaving the NAS to get ransomwared.