Today another attack on branch prediction engines of Intel CPUs from ASPLOS’18. This one, unlike the recent AMD vulnerabilities, seems to have been disclosed to Intel properly. A quartet of university researchers found another way to attack the branch prediction engine, including how to use the vulnerability to attack a secure portion of memory housed in SGX enclaves.
BranchScope Abstract
We present BranchScope — a new side-channel attack where the attacker infers the direction of an arbitrary conditional branch instruction in a victim program by manipulating the shared directional branch predictor. The directional component of the branch predictor stores the prediction on a given branch (taken or not-taken) and is a different component from the branch target buffer (BTB) attacked by previous work. BranchScope is the first fine-grained attack on the directional branch predictor, expanding our understanding of the side channel vulnerability of the branch prediction unit. Our attack targets complex hybrid branch predictors with unknown organization. We demonstrate how an attacker can force these predictors to switch to a simple 1-level mode to simplify the direction recovery. We carry out BranchScope on several recent Intel CPUs and also demonstrate the attack against an SGX enclave.
You can read the full paper here. It is interesting and we suggest a read.
If you are wondering what a SGX enclave is or why this is important here is a description the Intel SGX site:
“This Intel technology is for application developers who are seeking to protect select code and data from disclosure or modification. Intel® SGX makes such protections possible through the use of enclaves, which are protected areas of execution in memory. Application code can be put into an enclave by special instructions and software made available to developers via the SGX SDK.”
Intel’s Response to Branchscope
STH reached out to Intel about Branchscope earlier this morning and the company had this to say:
“[W]e have been working with these researchers and have determined the method they describe is similar to previously known side channel exploits. We anticipate that existing software mitigations for previously known side channel exploits, such as the use of side channel resistant cryptography, will be similarly effective against the method described in this paper. We believe close partnership with the research community is one of the best ways to protect customers and their data, and we are appreciative of the work from these researchers.”
This is another side channel exploit. It is highly likely that we are going to see more in the coming months as they are responsibly disclosed.

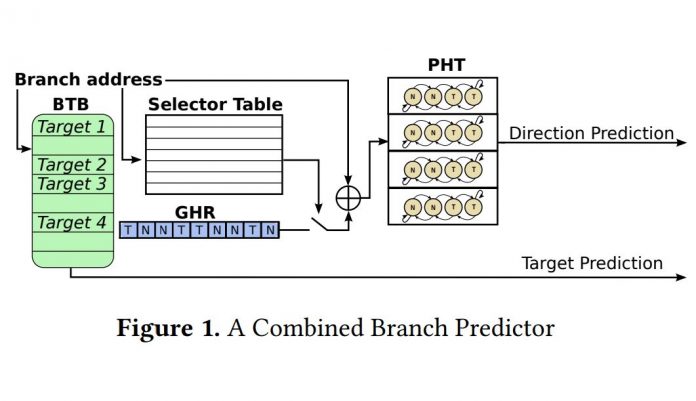



Sorry, but Intel’s answer contradicts what is in the paper. In the paper they say:
#1. “To the best of our knowledge, BranchScope is the first attack exploiting the directional predictor structure, showing that BPUs can be vulnerable even if the BTB is protected.”
than later in the paper:
“BranchScope is not affected by defenses against BTB-based attacks.”
#2. “We also demonstrate how BranchScope can be extended to attack SGX enclaves even if
recently-proposed protections are implemented.”
Intel on the other hand is saying:
“[We] have determined the method they describe is similar to previously known side channel exploits. We anticipate that existing software mitigations for previously known side channel exploits, such as the use of side channel resistant cryptography, will be similarly effective against the method described in this paper”