Java is extremely popular with IT equipment but a long history of self-signed certificates has made the Java Application Blocked issue annoying for admins everywhere. We recently had a short piece on how to fix the Java Application Blocked security feature for an individual IP address. This is useful when you have one server with a legacy IPMI interface and try to use KVM-over-IP or iKVM features. Yesterday I re-installed Windows 10 on my workstation and decided to make a script so that I could effectively turn off this security setting for my six main IPMI subnets. We have a ton of hardware from different vendors to test, but we also have legacy nodes to serve as load generators in different data centers. As a result, we run into this issue often.
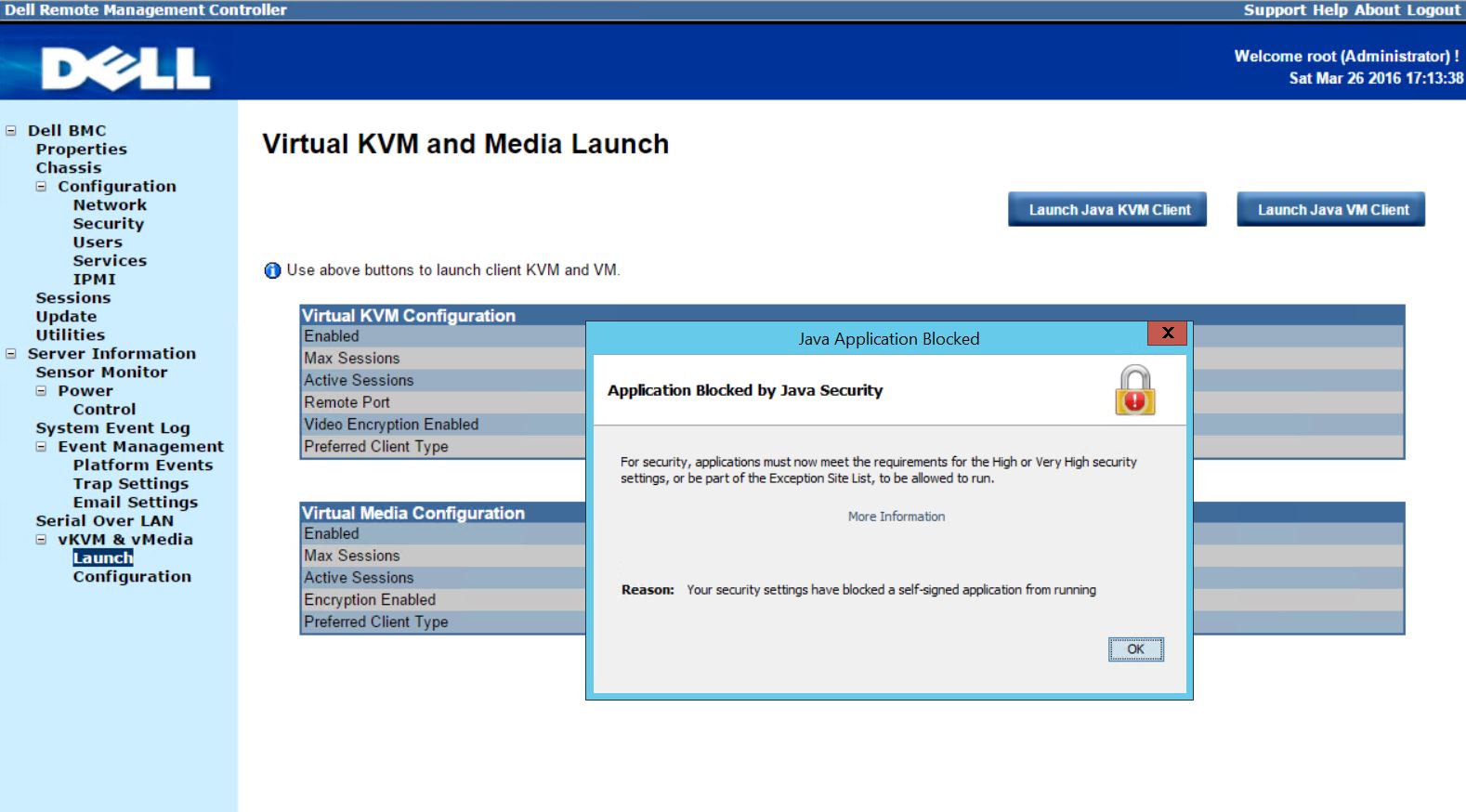
Background: Why am I getting the Java Application Blocked, Application Blocked by Java Security warning?
Legacy Java administration applications and tools often had self-signed certificates for their web launched applications. Since then two things have happened. First, Oracle began blocking self-signed certificates in standard security settings. Second, most servers/ server vendors have released patches with properly signed certificates. These patches require IPMI firmware to be upgraded which can be risky on a remote installation. Not all vendors have updated firmware available to fix this issue. Also, flashing a failed baseboard management controller (BMC) firmware flash means the BMC may become unresponsive. The fact that these certificates are blocked now by Oracle means that you cannot log onto iKVM or the Java app.
The real fix is to upgrade the BMC firmware or whatever Java application you are trying to run. If this is not possible here is the workaround.
How to workaround the Application Blocked by Java Security issue
To demonstrate the issue, we are using one of our Dell PowerEdge C6220 nodes which has an older self-signed Java application certificate. We navigate to Server Information -> vKVM and vMedia -> Launch via the Web GUI. One might notice this is not the standard iDRAC interface. The Dell PowerEdge C6220 was intended for cloud deployments and therefore came with a more industry standard Web IPMI interface. Form the appearance, we think it is running the Avocent BMC software.
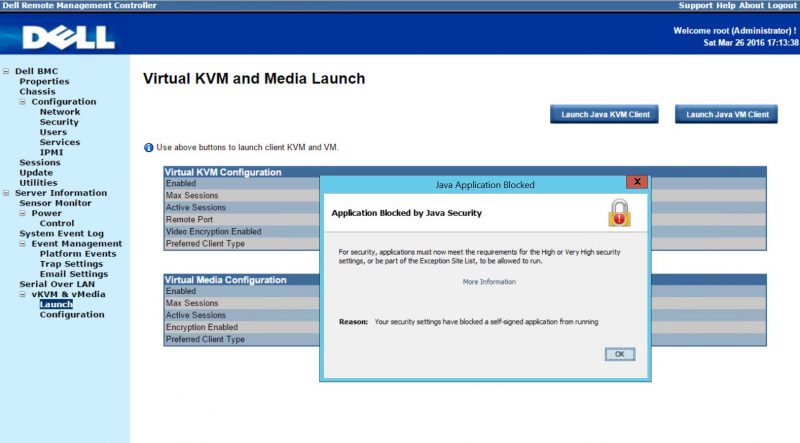
For fixing one server, this would not be too much of a hassle. You can simply follow our previous Java application unblocking piece. The Dell PowerEdge C6220 is a 4-node in 2U server so if you need to log into multiple servers, adding http and https entries can become time consuming. We tried using a wildcard, e.g. 10.0.1.* but that did not work with http or https.
How we stopped the Java Application Blocked on entire network subnets in 15 seconds
After installing Windows 10 from scratch, we realized that there was a need to make administration across our six IPMI interface subnets easier. We made a little loop in python that can be edited to stop this behavior.
Step 1 – make python file. I call mine byejava.py and this is the contents (I removed a bunch of IP ranges but here is the idea):
for x in range (1,254):
print ("http://192.168.1." + str(x))
print ("https://192.168.1." + str(x))
print ("http://10.0.1." + str(x))
print ("https://10.0.1." + str(x))
Each of the print statements should be indented if you are not seeing it displayed that way. You can see a properly formatted version in the STH forums resource.
Step 2 – From the command line, run the python script and create my new list:
py byejava.py > exception.sites
You can then move the output exception.sites file and replace the existing exception.sites file here (replacing username with your Windows username):
\Users\username\AppData\LocalLow\Sun\Java\Deployment\security
The best part is that if you have multiple machines (e.g. a workstation, a laptop and a management VM) you can use this exception.sites file in all of them and not have to worry about getting that blocker again. You can modify the for loop or even just the print statements to whatever IP address ranges you may want to use. There are two in the example above and depending on the device or application, you may need http or https unblocked for an IP address.
Warning and Disclaimer
To be clear, this will effectively disable a security feature on entire networks. Please do use this with care. We are not responsible if disabling your security settings results in some sort of malware or data loss. Use at your own risk and edit as necessary for your own needs and organizations security policies.
Where to go for more information
For more information, you can head to the resource in the STH forums. The resource has a better version of the script to use due to better code formatting. You can also add comments or questions to the associated thread.