We have been covering pfSense for many years on STH so every new release is a big event. Today we have the release of pfSense CE 2.6.0 and also pfSense Plus 22.01. For those that are unaware, the pfSense that is the “free” version is now the Community Edition (CE) while the Plus version is the paid version/ version that comes with pfSense approved appliances. We covered that here.
pfSense CE 2.6.0 Released Along with pfSense Plus 22.01
As for the changes, this feels more like a smaller set of changes with the big ones being around IPsec and ZFS. FreeBSD has supported ZFS for a long time so it is not a big surprise to see that pfSense is taking advantage of the robust filesystem.
- Numerous changes to IPsec for stability and performance
- Read the IPsec section of the Release Notes carefully
- IPsec VTI interface names have changed in this release. Configurations will be updated automatically where possible to use the new names. If any third party software configurations or other manual changes referenced the old IPsec VTI interface names directly (e.g. “ipsecNNNN”), they must be updated to the new format.
- IPsec status page and widget are significantly faster, show more complete information, and have additional useful functionality
- See the Release Notes and Development Notes for additional details
- ZFS is now the default filesystem for installations where possible
- New ZFS status dashboard widget (pfSense Plus only)
- New Disks widget to replace the disk usage list in the System Information widget
- This widget is automatically added and enabled if the firewall configuration contains the System Information widget with disk usage section active
- AutoConfigBackup no longer makes pages wait to load during the backup process
- The default password hash format in the User Manager has been changed from bcrypt to SHA-512
- Improvements to the Captive Portal logout page and process
- RAM disks have been converted to tmpfs (Source: Netgate)
To us, the big one may actually be the ZFS status dashboard widget. This is only in pfSense Plus, but it feels like a bit like a minor feature. Something that the ZFS change does impact is logging. With the swap to ZFS and compression on by default, ZFS is handling the log compression rather than the log rotation feature.
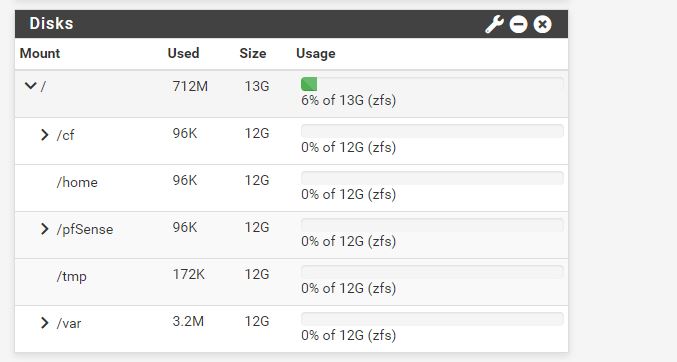
There is already a disks widget on the dashboard in the pfSense CE 2.6.0. Seeing the status of the underlying disks is interesting, but this is probably a feature that will be used by a smaller segment of users.
Final Words
Overall, new releases are good, but there seems like for pfSense CE users perhaps the biggest change other than default ZFS and the IPsec changes are going to be bug fixes. For those hoping pfSense 2.6.0 as a major dot release would bring a lot of new functionality running through the release notes looks mostly like bug fixes and minor enhancements. Of course, bug fixes are always welcome.
To get pfSense 2.6.0 you can download the ISO or upgrade in the Web UI. We suggest making backups before doing any upgrades. It is also usually wise when a new software version comes out to give it a few days before upgrading on remote systems just in case. Still, it great to see more development on pfSense.




Why did they downgrade the password hashing algorithm from bcrypt to SHA-512?
OPNsense had a release too, OPNsense 22.1 came with FreeBSD 13 underpinnings and Realtek driver updates for example.
I was just hoping for hardware support for the Intel i225 2.5GbE NICs in my new pfsense box.
I decided to upgrade my internal network to 2.5Gbps this year, and had a heck of a time before I realized I had to disable hardware acceleration for checksum offloading to get it stable with the new i225’s.
netgate already announced they are not going to be actively developing CE. They are going to close plus and put their efforts there. The lack of innovation in CE should not surprise anyone.
Why they downgraded password security is indeed a mystery
@HCS CE 2.7 is already available for netgate internally. Outside of the commercial use benefit with CE, it would be nice if the actually explained what the technical differences are between the two….i’ve heard some of the vpn wizards are a bit more polished and possibly some additional drivers.
@HCS show me where Netgate “announced they are not going to be actively developing CE.”
Hint: you can’t.
Hint2: I co-own Netgate
@Cheezehead differences are minor, atm. This will grow with time.
@Jon & @Wad I believe the change was due to compliance reasons for certain govt security requirements that specify using the CNSA suite.
@Bez, thanks for the information, but even still, it is a very poor decision. SHA simply isn’t meant to be used for password hashing, while bcrypt is explicitly made for it. For instance, SHA-512 by itself doesn’t use any sort of salt, so one has to implement that manually. If it really was about CNSA compliance, they could have made it optional and stuck with the much saner bcrypt as a default.
Just a note to anyone who is planning to upgrade from 2.5.2, the updated Realtek drivers that were introduced earlier are NOT included in 2.6.0 and Realtek NICs will be using the old buggy drivers again in 2.6.0.
I know it’s not ideal to run pfSense with Realtek NICs, but I’ve got a good deal on a box that had them and just wanted to put it to the test to see how good the updated drivers are and while I had absolutely no issues on 2.5.2, they started going down/offline after the 2.6.0 update.
Having good luck with the WAN Realtek interface on my Dell 3060-based pfSense 2.6.0, which I just updated to 22.01 a week ago. Also using Intel X520-DA2 for VLAN trunk.
dmesg.boot:
re0: port 0x4000-0x4
0ff mem 0xd3204000-0xd3204fff,0xd3200000-0xd3203fff at device 0.0 on pci2
re0: Using 1 MSI-X message
re0: turning off MSI enable bit.
re0: ASPM disabled
re0: Chip rev. 0x54000000
re0: MAC rev. 0x00100000
miibus0: on re0
rgephy0: PHY 1 on miibus0
rgephy0: none, 10baseT, 10baseT-FDX, 10baseT-FDX-flow, 100baseTX, 100baseTX-FDX
, 100baseTX-FDX-flow, 1000baseT-FDX, 1000baseT-FDX-master, 1000baseT-FDX-flow, 1
000baseT-FDX-flow-master, auto, auto-flow
re0: Using defaults for TSO: 65518/35/2048
re0: Ethernet address: xxxxxxxxxxxxxxxxxx
re0: netmap queues/slots: TX 1/256, RX 1/256
@Jon Looks like they are looking at changing it back or at least giving an option:
Original change: https://redmine.pfsense.org/issues/10298
Discussion about changing back: https://redmine.pfsense.org/issues/12800
From the OPNsense domain hijacking drama by pfSense parent, to constant whining of the owners/employees online over the years about various subject such as AES inclusion, slowly closing off the open source edition, etc – it is clear that moving to an alternative platform comes sooner than we may want. I’ve use pfSense since 1.2x days and as recent as 2.6. I was looking for something for my x86 low powered device and found x86 version of OpenWRT. Lo and behold, it actually performs superbly on 1:1 NAT DNAT style mapping for various servers in a company. The performance is excellent and the opk packing for adding more apps is great. Found the x86 and 64bit for great VLAN and routing for out large 1:1 requirement. Thanks pfSense but it looks like there are quite others willing to pick up where you left off.