If you are a VMware user, there is a good chance you have been impacted by the company’s latest security advisory. VMware Security Advisory VMSA-2017-0004.3 is listed as critical as it involves a remote code execution vulnerability. VMware is a relatively lightweight
About the Critical VMware Security Advisory VMSA-2017-0004.3
You can find the official page here. From that site here is the description:
Remote code execution vulnerability via Apache Struts 2
Multiple VMware products contain a remote code execution vulnerability due to the use of Apache Struts 2. Successful exploitation of this issue may result in the complete compromise of an affected product.
The Common Vulnerabilities and Exposures project (cve.mitre.org) has assigned the identifier CVE-2017-5638 to this issue.
Column 5 of the following table lists the action required to remediate the vulnerability in each release, if a solution is available.
In terms of applicability, it seems as though this is going to heavily impact vCenter 6.0 and 6.5 users.
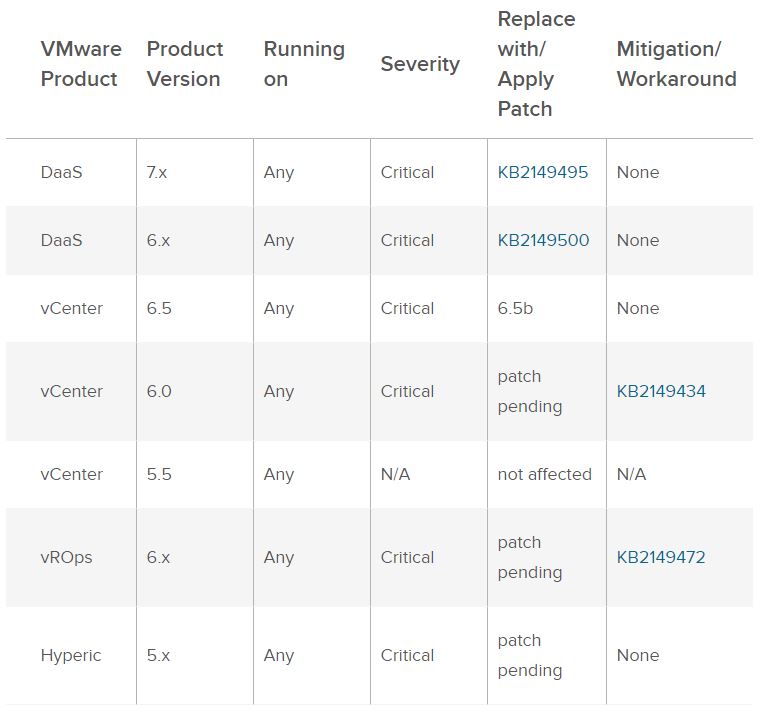
As you can see, the vulnerability hits some of VMware’s most popular virtualization and virtual desktop products. Remote code execution vulnerabilities are generally must-patch issues as they can enable malicious parties to remotely take over and control a server.
Here is the current changelog related to this issue:
2017-03-13: VMSA-2017-0004
Initial security advisory in conjunction with the release of workarounds for VMware vCenter Server 6.5 and 6.0.2017-03-14: VMSA-2017-0004.1
Security advisory update removing workaround for VMware vCenter Server 6.5 due to customer reported issues.
2017-03-14: VMSA-2017-0004.2
Security advisory update in conjunction with the release of VMware vCenter Server 6.5b.2017-03-15: VMSA-2017-0004.3
Security advisory update in conjunction with the release of HorizonDesktop as-a-Service Platform 6.1.6 fixes and a vRealize Operations Manager workaround.2017-03-16: VMSA-2017-0004.4
Security advisory update in conjunction with the release of Horizon Desktop as-a-Service Platform 7.0.0 fixes.