Microsoft acknowledged a major security issue concerning the Microsoft Malware Protection Engine. Here is the security bulletin 402234. What makes this vulnerability particularly scary is that it allows remote code execution from downloading files, emails, or from just about anywhere. The exploit was first found by a Google security research team and is present in multiple Windows versions including Windows 8, 10 as well as Windows Server versions. You can find more details here.
About the Microsoft Malware Protection Exploit
Here is a description of the exploit from CVE-2017-0290:
A remote code execution vulnerability exists when the Microsoft Malware Protection Engine does not properly scan a specially crafted file leading to memory corruption.
An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
To exploit this vulnerability, a specially crafted file must be scanned by an affected version of the Microsoft Malware Protection Engine. There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine. For example, an attacker could use a website to deliver a specially crafted file to the victim’s system that is scanned when the website is viewed by the user. An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.
If the affected antimalware software has real-time protection turned on, the Microsoft Malware Protection Engine will scan files automatically, leading to exploitation of the vulnerability when the specially crafted file scanned. If real-time scanning is not enabled, the attacker would need to wait until a scheduled scan occurs in order for the vulnerability to be exploited. All systems running an affected version of antimalware software are primarily at risk.
(Source: Microsoft)
How to Protect Yourself
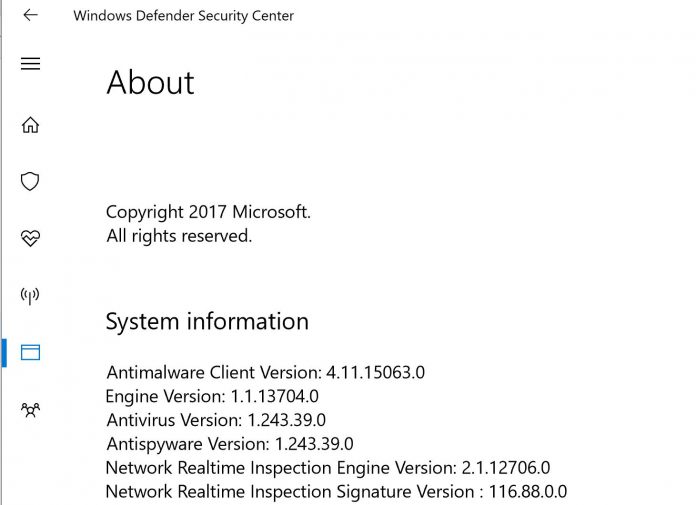
Microsoft released a Windows Defender engine update. You will want to be on version 1.1.13704.0 or later. Here is an example:
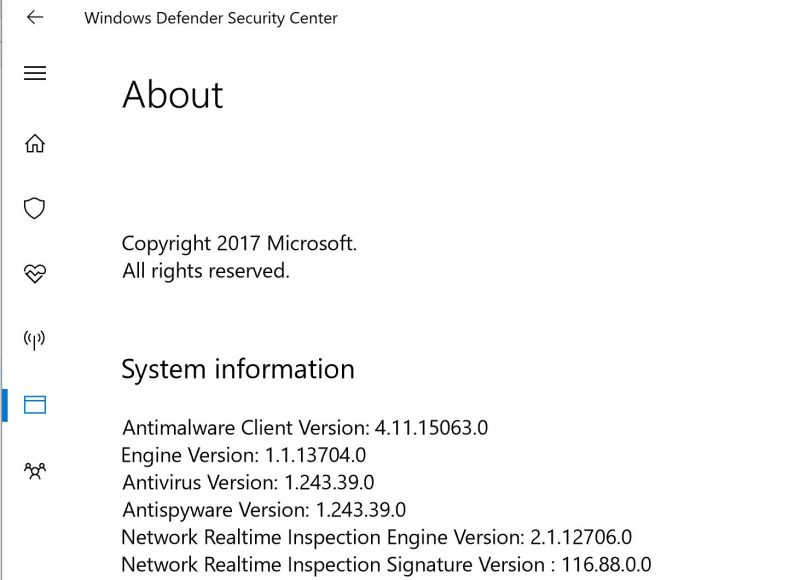
In Desktop OSes, you can find your version on the About page of Windows Defender. Generally, this is software updated automatically on a monthly basis and with the ability to push updates in the background. As a result, for most Windows users it is already patched. If you have a corporate system where you are delaying or stopping this automatic update functionality for machines, we suggest getting this patched on impacted machines as soon as possible.