TP-Link Omada VPN Gateway ER8411 Performance
First off, we tried just passing traffic through the gateway at full 10Gbps speeds to see if we could do that with IDS off.
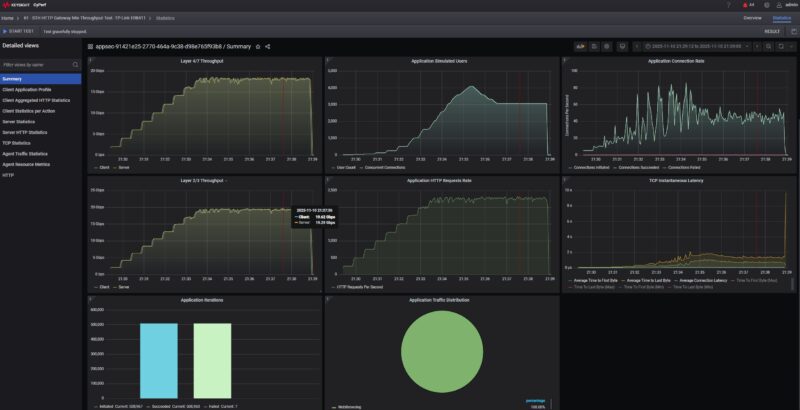
This was not an issue at all and the gateway passed standard HTTP(S) bidirectional 10Gbps of traffic with ease.
The next step was turning IDS and IPS onto high to see if there would be an impact to the performance.
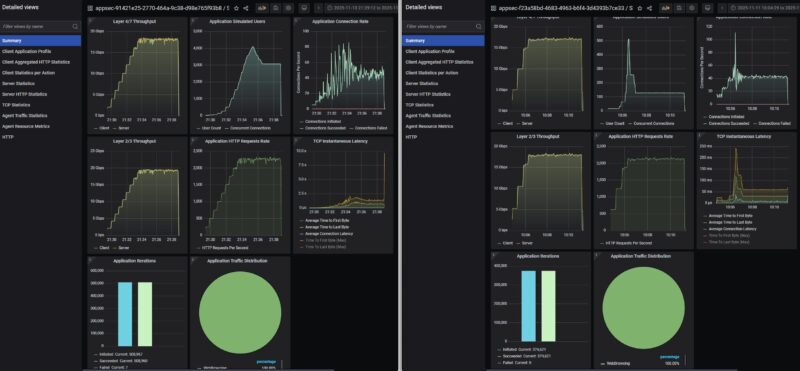
A few things to note here. First, the throughput dropped by about 2Gbps. Also, you will see that as the users/ connections scaled, we got large latency spikes and so CyPerf backed off the device.
We then added deep packet inspection to the setup.
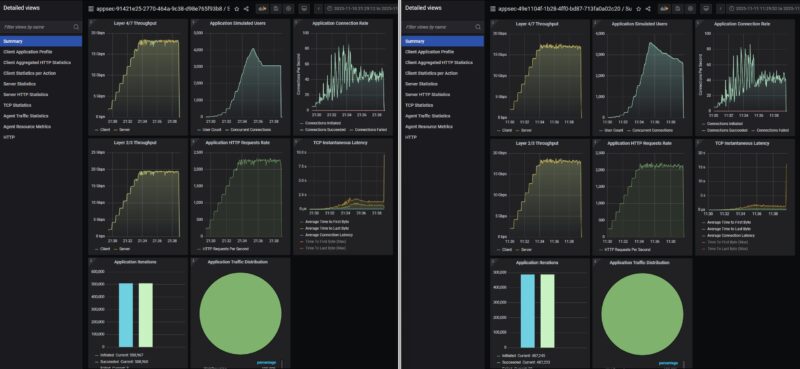
There was really not much of a change here versus just turning on the IDS/IPS, but we wanted to see what checking the box on the DPI setting would do.
We then tried our standard low-end STH gateway device review 11 app mix of ChatGPT, Google Drive, Google Sheets, LinkedIn, Netflix, Office365 Outlook and Calendar, Reddit, X.com, and YouTube. With all of the security features, turned on, we hit around 10Gbps of traffic.
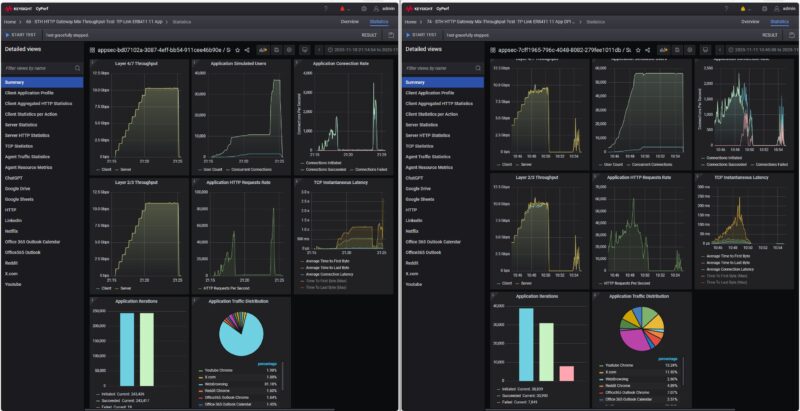
When we turned on the security features onto high, we saw something really interesting. First, the maximum throughput dropped by around 1-2Gbps again. The bigger change is that after some time, some of the traffic failed, and then the device just stopped passing traffic. After a few minutes, the traffic picked back up, but at a much lower rate then we were still getting failed connections.
We ran this a few more times, restarting the unit between the runs. We also wanted to turn the DPI feature on as well to see what would happen.
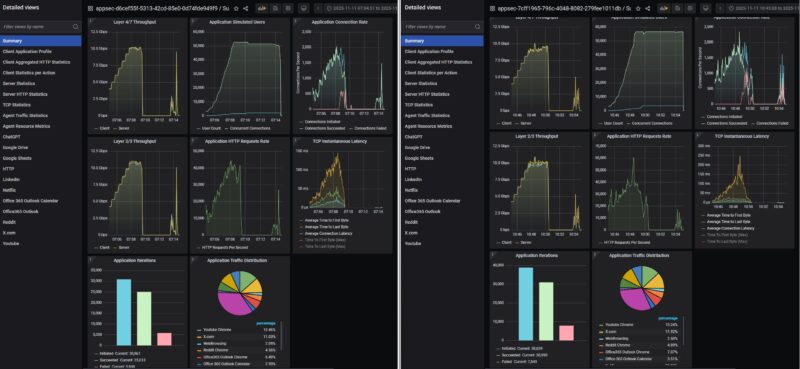
With the DPI setting turned on, we lost some performance again, but we saw a similar pattern where connections were getting dropped then a trickle of traffic would get through.
Just as a note, we did not turn on the attack profiles for this, it just happend repeatedly during our testing and we thought it was a really interesting result worth sharing. Of course, running a gateway at 100% for this long would create a rough user experience. At the same time, it shows why it is important to use real-world traffic when testing firewall features.
TP-Link Omada VPN Gateway ER8411 Power Consumption and Noise
In terms of power consumption, at idle we saw around 12.3W, which is decent for at 10Gbps gateway.

With one 1GbE port connected, we got 12.6W.

Connecting a SFP+ to 10Gbase-T device, we saw an increase of 1W to 13.3W.

Overall, this is decent power consumption and what we would expect from a device like this.
Final Words
What a cool review on a number of levels. First, we found a device that is 10Gbps capable and certainly delivered that with simple traffic. We were able to see how turning on some relatively basic firewall features had a direct impact on the performance. We also saw something really neat as the combination of applying the firewall features and the real-world traffic under high-loads we managed to get the TP-Link to stop passing traffic. Again, this was without adding attack profiles into the mix which made it really interesting.

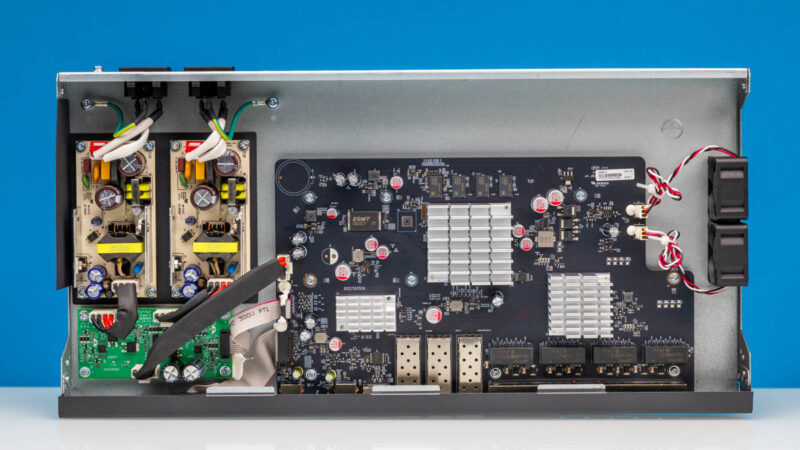
In terms of the hardware, TP-Link has a decent design, but we wish it would switch to screws or clips so anyone can inspect the hardware. At least that will let folks inspect their own hardware, which would be useful given some of the pressure on TP-Link.
Hopefully folks find this interesting. This is a great case of how using a (significanly) higher-end traffic generation tool is getting us more interesting data. We will keep stepping up the intensity in future reviews, but we thought this was a neat box to review.
Where to Buy
Here is an Amazon affiliate link to what we purchased.




There is a 4-pin serial header to the top left of the main chip/heatsink – be great if you were able to grab the boot log from devices and post them up so folks can see what they run ‘under the hood’